Hello everyone, I just wanted to discuss some vulnerability I found and exploited for GOODNESS .. just so that SCRIPT KIDIES won’t attack your home/business network .
Well, in Algeria the main ISP ( Algerie Telecom ) provide you with a router when you pay for an internet plan. So you can conclude that every subscriber is using that router . TD-W8951ND is one of them, I did some ip scanning and I found that every router is using ZYXEL embedded firmware.
Analysis :
Let’s download an update and take a look at it and try to find some vulnerabilities. ( http://www.tp-link.com/Resources/software/TD-W8951ND_V3.0_110729_FI.rar )
The ras file is in LIF format !! …
Hmmm let’s put that file for Binwalk test for God’s sake ! ( check : http://code.google.com/p/binwalk/wiki/Installation for more informations on how to install it ).
This is what Binwalk told me about that file :

You can clearly see and confirm that the router is using zynos firmware. We can also see that there is two blocks of LZMA compressed data … let’s extract them and have a look.

The problem is that when I tried to decompress the two blocks I get an error : ” Compressed data is corrupt “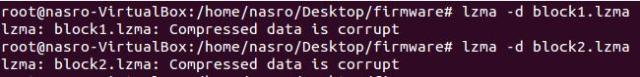
Hmm, first the “ras” file was in LIF format .. and now the lzma compress blocks are corrupted !!
I googled this and tried to find a solution for this, FOUND NOTHING . How am I going to solve this ??
One idea came in my mind .. “Strings” command and here is what I got :
Aaaah ! so the blocks aren’t compressed with LZMA or anything ! and the whole “ras” firmware file is just big chunk of data in clear text.
Ok, let’s try and find some useful STRINGS …
After some time searching “I” didn’t find the useful thing that will help us find vulnerabilities on the firmware !!
I didn’t give up …
I just was thinking and questioning :
- Me: What do you want from this firmware file !
- Me: I want to find remote vulnerabilities that will help me extract the “admin” password.
- Me: Does the web interface let you save the current configuration ?
- Me: yes !!
- Me: Is the page password protected ?
- Me: No !!! I tired to access that page on a different IP and it didn’t require a passowrd !
Ok, enough questions haha ..
Now, when I activated TamperData and clicked “ROMFILE SAVE” I’ve found out that the rom-0 file is located on “IP/rom-0” and the directory isn’t password protected or anything.
So we are able to download the configuration file which contains the “admin” password. I took a look at rom-0 file and couldn’t figure out how to reverse-engineer it, and when you don’t know something it’s not a shame to ask for help .. and that’s what I did !
I contacted “Craig” from devttys0.com, he is an expect when it comes to hacking embdded devices . He’s a great guy and he replied to my email and pointed me to http://50.57.229.26/zynos.php which is a free rom-0 file decompressor .
When you upload and submit the rom-0 file there, the php page replies back with the configuration in clear text ( INCLUDING THE PASSWORD ) .
So what i need to do now is to automate the process of :
- Download rom-0 file.
- Upload it to http://50.57.229.26/zynos.php
- get the repy back and extract the admin password from it.
- loop this process to a range of ip addresses.
And that’s exactly what I did, I opened an OLD OLD poc python script of mine that accessed routers via telnet using the default passwords. So what I just need to do now is to add some functionality to it.
Well I thought about this, and I’m posting this script online ONLY FOR EDUCATIONAL PURPOSES.
You can find the scripts here : https://github.com/MrNasro/zynos-attacker/
Demo :
PS : I OWN ALL THE IP RANGE I WAS SCANNING ” FOR SURE 😉 “
Prevention :
Now ! how do you prevent attackers from downloading your rom-0 configuration file and manipulating your router ? This is pretty simple if you think about it ..
You just have to forward port 80 on the router to and inused IP address on your network :
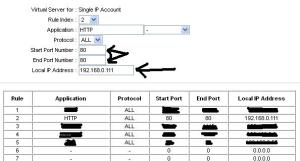
THATS ALL, or if you want to play a little with attackers that are using scripts too .. just forward port 80 to you local http server and put a LARGE file in the root directory and name it rom-0 .. just let them download like 1GB rom-0 file haha haha .. I have also automated the process of port forwarding and I’m running the scripts daily just to prevent hackers from attacking weak users …
In the next post I’ll demonstrate how would a malicious hacker exploit this to hack TONS of networks and get a meterpreter/reverse_shell on every PC on the target network ..
Hope you enjoyed this analysis, if you have anything to add or any questions to ask don’t hesitate to contact me ! BE THEIR HERO, HAPPY HACKING 😉
UPDATE:
The decoded.php script is now located at : http://198.61.167.113/zynos/decoded.php , I have updated the code.py script



the script is not working
How we can automate port forwarding? What command we should use?
Thanks for the great article!
Hi Root@Nasro,it’s a Great POC 😉 , But:
1) I think You’ll encourage Some Kids To F**k Algerians A**es 😀 , Since not all kind of People will Read Your Blog ;). if you don’t care will,So, will be nice for Black Sambrero :D, & “Flash player Update” Virus.
2) I suggest the Use of the ACL part, & accept only LAN access for all interfaces, bCoz i think redirect Port 80 didn’t Solve the entire problem.
3) After All You are a Good Programmer,& it’ll be a Great Project if you Code Some Scripts To fix the Problem Remotly (For educational Purposes Only 😉 ), Will be nice if you share This script ;).
Good Luck
thank you for you info. it helped me a lot but many routers don’t have your web interface so I used CLI to solve it & I published it there
For future reference. Here is a link that explain the rom-0 data extraction for the zxv10 w300 model (it’s in spanish though), that it’s the same on this article: http://pastie.org/7300059
Btw, archive.org’s way back machine works just fine to read Kender’ original article (and source): https://web.archive.org/web/20120222220908/http://everlost.nl/kender/zyxel
Hey there, You’ve done an excellent job. I will certainly digg it and personally
recommend to my friends. I am confident they’ll be benefited
from this web site.
If some one desires to be updated with newest technologies then he
must be pay a visit this web site and be up to date every day.
Thanks for sharing your thoughts about pay day.
Regards
you could try reinvent the wheel
There is a Windows tool: http://www.mrtcll.com/zynos-rom-0-scanner.html
Some guy from Indonesia(maybe?) created a website to automate this “download rom” and “decompress” process.
I’ve tried once and it works, you should give it a try, the only thing to do is to input the target’s public IP.
url is: http://speedy.ml
Salam, il faut aussi rediriger le port 8080 (105.107.xxx.xxx:8080/rom-0) #AlgerianHacker.
This is the perfect blog for nybody who would like tto fijd out about this topic.
You know so much its almost tough to argue with you (not that I actually will need to…HaHa).
You dwfinitely put a fresh spiun on a subject which has been discussed for years.
Great stuff, just excellent!
Thank you 🙂
sir i use teracom tdsl300w2 router and i have been hacked a few times now..i used an antivirus which told me about this rom0 vulnerability in my router but i dont have any idea about how to protect it .i read your pos regarding port forwarding, sir cud u please explain i to me in detail it wud be a great help.sir please explain with what u meant to say in this line ” .. just forward port 80 to you local http server and put a LARGE file in the root directory and name it rom-0″ how to put the file in the root directory.
Someone made similar tools to automate whole process here: http://speedy.ml
I just need to input the target’s IP address and the tools will get the password.
Hi! Your article is most enlightening. Had a doubt though: if I forward port 80 to an unused IP address in my network, would that also not stop me from accessing the web-based router admin page? i.e., along with essentially turning http://IP/rom-0 into a dummy, will it also not turn http://IP into the same? In that case how would I administer the router?
I seem to be the unfortunate victim of Misfortune Cookie and so trying out different things to make my router safer, since there is no scope to upgrade the firmware.
Hello,
You will still have access to your router through the internal IP ( 192.168.1.1 by default ) the forward only takes place when you try to access the router from external IP
http://egyptianvulture.blogspot.com/2014/06/how-to-fix-zynos-vulnerability-prevent.html
Wow! Thanks! Maybe THAT’s the reason why my router constantly being DNS-hacked!
It’s TP-Link TD-W8901G and I’m shocked that I had to create 20 symbols passwords which were so easy to read by anyone!
Thanks for that!
BTW. Is it OK if after fixing with your Port-Forward Method I can still download rom-0 file without enetering password from computer connected by cable?
OMG man I love you 😀 😀 😀 lets playy game whit my friend 😀
Hello, I have one of these routers on my home network. While I was able to reproduce the exploit from inside the local network I can’t seem to obtain the rom-0 file from the outside.
I’m trying to curl $SSH_CONNECTION and $SSH_CONNECTION/rom-0 while I’m SSH’ed into a remote server (this environment variable holds my router’s external IP), but it appears that by default the router does not even respond to HTTP requests sent to its outer interface, which seems reasonable to me. How did you manage to fetch the rom-0 file from outside the LAN?
Hey, anyone tried this with a Zyxel P-2812HNU-F1 which seems functioning, but likely has ISP firmware and passwords to access setup page? The standard Zyxel factory reset doesnt work. Should default to admin/1234.
I would like to find user name and password.
Any ideas would be great.
I’m a relative noob at this….
The level of what I’m going to ask is something to be ashamed of, compared with the technicality of your article. Nevertheless…
1. I haven’t been able to forward port 80 to an unused IP. To be honest I don’t even know what range is used and what not – I assume all 192.168.0.xxx.
I have a TP-LINK “TD-W8901G” and below (translated in English) is the message I get:
Note: CPE’s HTTP WAN port will be changed in 8080 if correctly introduced.
I get it when I try to save changes.
unfortunately This is not a solution the same IP can be accessed through 8080 port and in the same time you can’t block both 80 and 8080 plus there are other ways to download rom-0
I am really loving the theme/design of your blog. Do you
ever run into any internet browser compatibility issues?
A couple of my blog audience have complained about my site not working correctly in Explorer but looks great in Safari.
Do you have any advice to help fix this issue?
can you share with us the version of this firmware TD-W8951ND_V3.0_110729_FI.rar ) ? I cant download it
i put your firmware anyways not work